Failed authentication or authentication loops
Applies to
Any OSLC application
Problem
User authenticates to the remote application, but the authentication does not appear to be working.
While OSLC Connect applications and ELM will enter a login loop, Polarion will display the following:
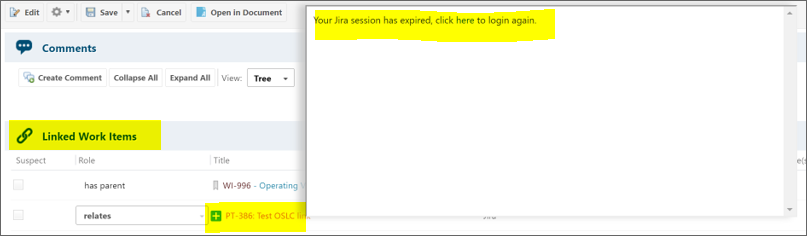
Cause
There can be various causes to this. To get a proper root cause, please review the following possible causes:
A popup to authenticate to your OSLC Connect application is closed or blocked
The authentication popup can be blocked by your browser.
If the browser popup blocker was enabled and you disabled it, or if there was a plugin acting as a popup-blocker and you disabled it, please try the failing interaction again.
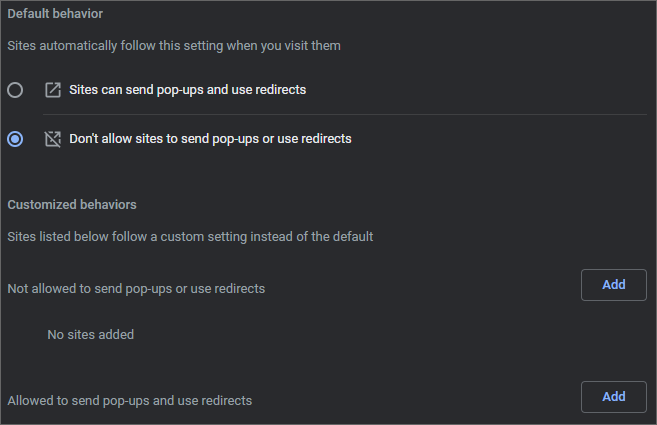
There are blocked cookies in Chrome
Cookies are what is used by a given application to store its authentication. If the cookie is blocked, it cannot be used when navigating an OSLC application to interact with another OSLC application.
If you see blocked cookies when navigating there just after you experienced the authentication problem, you will need to select the cookies, then click Allow.
Unfortunately, as of now, this procedure has to be performed by all impacted users.
Applications live on different domains
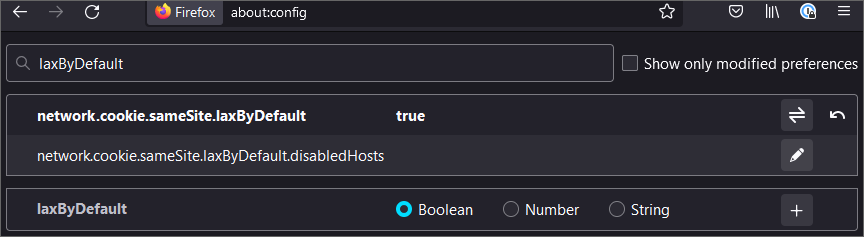
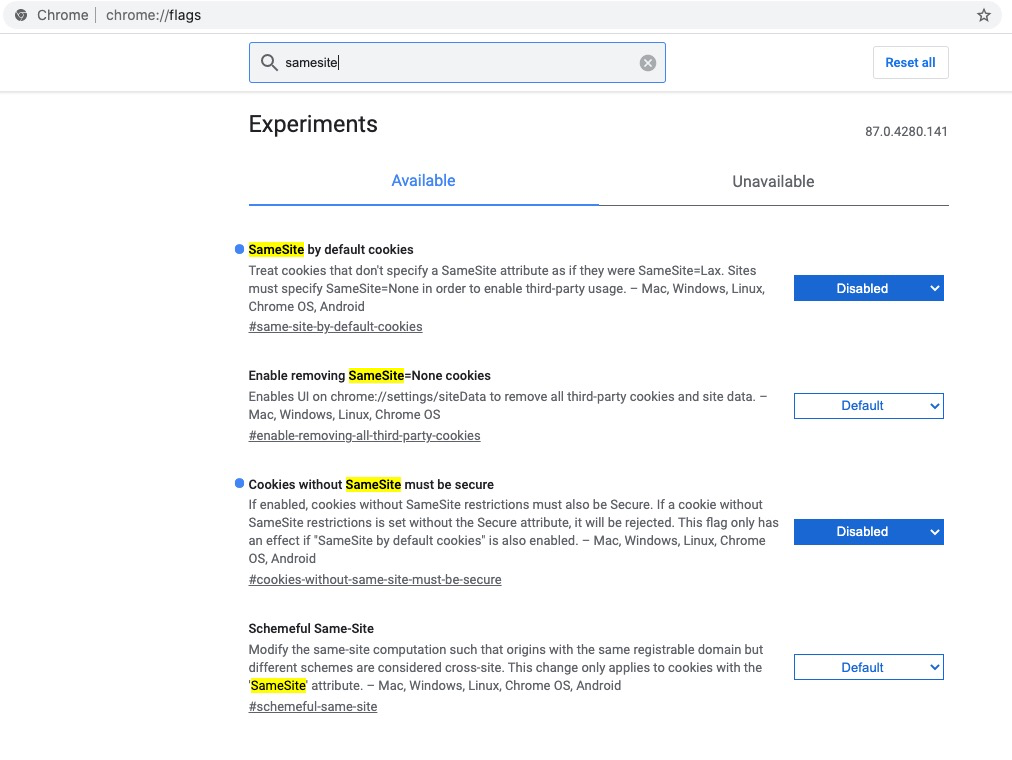
As mentioned in the above section, cookies are what is used by a given application to store its authentication. When that authentication needs to be shared by another site, as is needed between an OSLC client and an OSLC server in the OSLC interactions, and if those applications live on different domains, browsers will consider this is a 3rd-party attempting to use a cookie which is not his, and may prevent such usage as a security measure. This will default to a failure in Chrome, and may also break in Firefox if the corresponding security feature has been enabled.
If no, you may want to review the load balancer configuration, if any. Some OSLC Connect applications are deployed on Atlassian on-premise applications, where the Traffic Distribution feature may have been enabled. Unfortunately, that feature is currently not compatible with our OSLC Connect application. If the problem persists after you checked the load balancer, please reach out to us by creating a support request.
If yes, proceed with the below.
If your OSLC Connect application was already “SameSite=None enabled” at the application server level, that configuration should be removed. Since the release of the Security feature in our OSLC Connect products, we recommend customers to disable any former configuration and rely on that Security feature, which provides better security for OSLC Connect products. If you don’t know about that, it is likely not the case.
Note that depending on the version of Firefox, this either means that Firefox is not requiring the “samesite=none” property on cookies, or that Chrome is blocking cookies for some reasons.
You can use your browser to confirm the cause, as suggested below.
If enabling the above features in an unaffected browser triggers the problem, or vice versa if disabling it in an affected browser resolves the issue, you will find more details about the cause as well as a resolution in Embedded Content or Authentication Isn't Working between OSLC Applications.
If there was no blocked cookies, and you happen to experience the problem, please reach out to us by creating a support request.